(“Facebook’s Acquisition of Instagram Just Another Question Mark for Internet Privacy”)
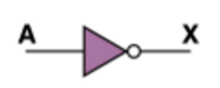
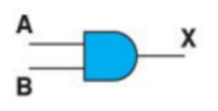
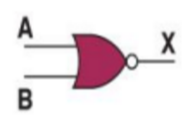
Today, we discussed about an ethical topic in our CS class: “Is privacy a past thing?” Mr. Lin first lead our discussion by stating a phenomenon: Some online services and social networks, which are so popular and convenient that we cannot give up using, may store and sell our private information to gain profit, but we may never know that. Sometimes we receive advertising calls from people who know our name and even our age. Where do their information comes from? Definitely, they bought from some services that we are using. Those companies may sell our private information without our permission. And our information in the company’s database may be stolen by hackers. It’s almost true that if we use the services on the internet, we will have the possibility to lose our privacy.
Mr. Pete made a very good point that we should try to choose the services provided by good companies that we trust. And when we want to use a new service that we don’t know its credibility, we should always read the “terms of use” before clicking on the check box. In addition, we should pay attention to the news to know if the services we are using have bad reputation about customers’ privacy. It is actually a skill that we can distinguish the good and bad companies by carefully investigating and judging.
Base on the fact that there is no 100% privacy on the internet, we should learn how much we should put our personal information on the internet. We should be aware of the danger to post our personal information – location, email-address, phone number, or passwords – on the social network. We should also be careful when a website or an app asks us to type in our private information mentioned previously.
Furthermore, Lin thinks that the government have the absolute power to access some of our private information. He asks us if that is a good thing. Personally speaking, I think the government is protecting us through monitoring people’s behaviors on the internet. By doing so, it will be much easier for the government to prevent crimes and ensure national security. All of our class agree this idea, and we choose to believe that the government is doing the right thing.
Coming back to the topic: Is privacy a past thing? To answering this question, we should know what privacy means. David and I hold the same opinion that privacy’s definition is changing over the time. Some information that we used to think is private now become “public” information that is exposed to everyone on the internet. I don’t think privacy is a past thing, because there is never absolute privacy and we will never be totally transparent. The point is that our ways of communicating is changing, and our privacy is getting easier to be accessed by others. What we should do is to be aware of this fact and be more cautious when we share our information on the internet.
Work Cited
Facebook’s Acquisition of Instagram Just Another Question Mark for Internet Privacy. AppAdvice, 10 Apr. 2012, http://appadvice.com/appnn/2012/04/facebooks-acquisition-of-instagram-just-another-question-mark-for-internet-privacy. Accessed 24 Sept. 2016.